NCERT Solutions For Class 11 Business Studies Emerging Modes of Business
TEXTBOOK QUESTIONS SOLVED
I.Multiple Choice Questions
Tick mark (✓) the most appropriate answer to the following questions:
Question 1. e-commerce does not include:
(а) A business’s interactions with its suppliers
(b) A business’s interactions with its customers
(c) Interactions among the various departments within the business
(d) Interactions among the geographically dispersed units of the business
Question 2. Outsourcing:
(a) Restricts only to the contracting out of Information Technology Enabled Services. (TIES)
(b) Restricts only to the contracting out of non-core business
(c) Includes Contracting out of manufacturing and RandD as well as services processes -both core and non-core, but restricts only to domestic territory
(d) Includes off-shoring
Question 3. The payment mechanism typical to e-business
(a) Cash on delivery!CoD) (b) Cheques
(c) Credit and Debit Cards (d) E-cash
Question 4. A Call Centre handles:
(а) Only in-bound voice based business (b) Only out-bound voice based business
(c) Both voice based and non-voice based business (d) Both customer facing and back-end business
Question 5. It is not an application of e-business:
(a) Online bidding (b) Online procurement
(c) Online trading (d) Contract RandD
Answer:
1. (c) 2. (b) 3. (d) 4. (d) 5. (d)
II. Short Answer Type Questions
Question 1. State any three differences between E-business and traditional business.
Answer: The differences between e-business and traditional business can be summarized as below:
- Logistics: The logistics of e-business typically have lesser constraints than traditional business. E-businesses are not limited to venue; they can be located anywhere and still serve the same customer. Their product capacity is “infinite” in that they are not limited to the space of a brick-and-mortar store. E-businesses mainly depend on shipping methods to deliver and receive items, while traditional stores conduct an instant exchange. This timing difference can be a significant factor for some consumers. For example, refunds would typically take much longer to process for e-businesses than in a neighborhood store.
- Human Resources: The two types of business differ in talent recruitment. E-businesses significantly emphasize technology and hire more people from the web design and development fields. In some cases, every employee may be required to have a technical background or receive in-house training for basic web development. On the other hand, traditional businesses are more diverse in hiring for non-technical positions, such as sales representatives and display managers.
- Marketing and Finance: In marketing for traditional business, marketers can focus on all five human senses to influence the sale. For example, maintaining a proper display keeps the product aesthetically appealing. Consumers can also physically touch the product in a traditional store; this is particularly vital for physically sensitive items such as clothes. E-businesses typically have to rely mainly on sight. The physical display is replaced with digital images. The inability to touch and test the product first hand is replaced with technical text to visualize the details of the product; online retailers may also have the ability to present many more choices because they do not need to have the physical product on hand.
The major financial difference between e-business and traditional business is cost. E-businesses usually have lesser start up and operational costs, buying an online domain is much cheaper than renting land and building facilities and buying equipment. - Management: E-business management is typically flatter than traditional management. A flat company happens when there are few levels in between top management and the entry-level employee. In most E-businesses, low level management, such as store managers and division managers, is unnecessary. Instead, E-businesses expand horizontally by hiring external consultants and contract web development positions. These entities specialize in a business service, such as e-commerce setup and online marketing. They may work for the company but are not necessarily included in or affected by management decisions.
Question 2. How does outsourcing represent a new mode of business?
Answer: Outsourcing represents a new mode of business. It is fast becoming an emerging mode of business. Firms have started increasingly outsourcing one or more of their processes which can be efficiently and effectively carried on by others. Outsourcing can be qualified as emerging mode of business because its acceptance is increasing as a fundamental business policy and philosophy, as opposed to the earlier philosophy of doing it all by yourself.
Question 3. Describe briefly any two applications of E-business.
Answer: Two applications of E-business are discussed below:
- e-Procurement: It involves internet based sales transactions between business firms including both, “reverse auctions” that facilitate online trade between a single business purchaser and many sellers, and, digital market places that facilitate online trading between multiple byers.
- e-Delivery: It includes electronic delivery of computer software, photographs, videos, books (e-journals) and other multimedia content to the other’s computer. It also includes rendering of legal, accounting, medical and other consulting services electronically. In fact, internet provides the firms with opportunities for outsourcing of a host of Information Technology Enabled Services (ITES).
Question 4. What are the ethical concerns involved in outsourcing?
Answer: Following are the major ethical concerns involved in outsourcing:
- Confidentiality: When a company outsources any of its functions, it has to share a lot of information and knowledge with outsourcing partner. He may not preserve confidentiality. If company adopts outsourcing of complete processes or products, there is further risk that outsourcing partner may start his own business which may increase competition.
- Sweat Shopping: The firms which opt for outsourcing aim at lowering their costs, try to get maximum benefit from the low cost manpower of the host countries. Secondly, such works are outsourced which do not build much of competency and ability of outsourcing partners. So, they build blue collar workers by handing over doing skills rather than creating white collar workers by transferring thinking skills.
- Using Child Labour and not following Labour Laws: Outsourcing is engaging child labour and women in the factories. Moreover, there exists wage discrimination on the basis of sex of the worker. Workers are exploited by giving less than minimum wages.
- Resentment in the Countries: When MNC& contract out manufacturing, marketing, accounting, R and D etc. to developing countries, it may create resentment in home country. The people from developed countries may not like that the jobs which they could get have been transferred to developing nations for cost cutting.
Question 5. Describe briefly the data storage and transmission risks in E-business.
Answer: In the present century, information is acting as power. If the relevant information of the business reaches into wrong hands, it may create a lot of loss for the company concerned. There is a risk of en route being stolen or modified by wrong people for their selfish motives. It is exposed to the risk of VIRUS and hacking. VIRUS stands for Vital Information Under Seize. Installing and timely updating anti-virus programmes and scanning the files and disks with them provides protection to the files, folders and systems from the attack of virus.
Another risk involved is interception of data in the course of transmission. To protect data against this, cryptography is used. Cryptography refers to the art of protecting information by transforming it into an unreadable format called ‘cyphertext’. Thereafter only those who have a secret key can decrypt the message into ‘plaintext’. It is like coding and decoding.
III. Long Answer Type Questions
Question 1. Why are E-business and outsourcing referred to as the emerging modes of business? Discuss the factors responsible for the growing importance of these trends.
Answer: E-business and outsourcing are referred to as emerging modes of business. Prefix ‘emerging’ puts emphasis on the fact that these businesses are in the process of development. These changes are happening here and now, and, that these changes are likely to continue. In fact, three changes are taking place most strongly:
- Digitizaton: The conversion of text, sound, images, video and other content into a series of ones and zeroes that can be transmitted electronically.
- Outsourcing: Contracting out non core activities to outside firms.
- Internationalisation and globalisation: More and more foreign companies are entering into India and sending Ashia and Indian companies becoming MNCs. Therefore, E-business and outsourcing referred to as the emerging modes of business.
Following factors are responsible for the growing importance of these trends:
- Improvement in Information Technology: With the improvement in information technology and emergence of internet the process of outsourcing and e-business is on an expansionary path.
- More and More Interactive Websites: Websites are becoming more and more interactive. It is removing the problem of ‘low touch’.
- Improvement in Communication Technology: Communication technology is continually evolving and increasing the speed and quality of communication through internet.
- Diffusion of E-Commerce in all nooks and corners of the country: In order to diffuse e-commerce in all nooks and corners, India has undertaken about 150 such projects. It is also growing importance of these trends.
- Global Competitive Pressures for higher quality products: Due to adoption of new economic policy of 1991 in India, there has been an increase in competitive pressure from giant sized MNCs and global enterprises.
- Ever Demanding Consumers: There is increasing demands from consumers for high quality products at minimum cost. Therefore, e-business and outsourcing are being chosen as newer options. But e-business and outsourcing are not emerging out of compulsion but also out of choice because of its benefits to consumers as well as producers.
Question 2. Elaborate the steps involved in online trading.
Answer: Operationally, following steps are involved in online trading: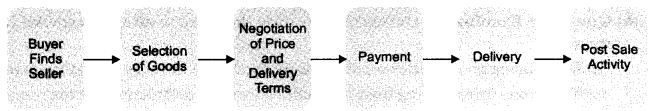
- Registration: First step in online trading is registration with the online trader by filling up a registration form. With registration buyer has opened an account with online trader. A password is created for the account which protects account and shopping cart which can be misused otherwise.
- Placing an Order: An account holder can drop the items in the shopping cart. Shopping cart is an online record of what a person has picked up while browsing the online store. Once being sure of what a person wants to buy, one can check out and choose his payment options.
- Payment Mechanism: In online trading payment may be made in any of the following ways:
- Cash On Delivery: Under this, the payment for goods ordered online may be made in cash at the time of physical delivery of the goods.
- Cheque: Another option is that the online vendor may arrange for the pickup of the cheque from the customer’s end. Upon realization, goods may be delivered.
- Net Banking Transfer: These days banks provide facility to the customers for electronic transfer of funds using internet. Therefore, a buyer can also make use of net banking money transfer to pay for the goods ordered.
- Credit or Debit Cards: These are also called plastic money. These cards are most popularly used in payment for online transactions. To accept credit card as an online payment type, the seller first needs a secure means of collecting credit card information from its customer. Payments through credit cards can be processed either manually, or through online authorization system like SSL Certificate.
- Digital Cash: It is a kind of electronic currency which exists only in cyberspace. It has no real physical properties, but offers the ability to use real currency.in an electronic format. For this, the buyer has to deposit cash in bank account which issues equivalent digital cash to the person which can be used for online trading. It is more secure than credit or debit cards.
Question 3. Evaluate the need for outsourcing and discuss its limitations.
Answer: Outsourcing has emerged as a way of doing business due to global competitive pressures for higher quality products at lower costs, ever-demanding customers and emerging technologies. Need for outsourcing can be understood from the benefits which are given below:
- Focusing of Attention: Business firms are realizing the importance of focusing on core areas where they have distinct ability and core competence and contracting out the rest of the activities to their outsourcing partners. A business organization needs to decide its core areas and non-core areas. Once they outsource non-core areas, they can focus their attention on selected activities. It will increase efficiency and effectiveness.
- Quest for Excellence: Outsourcing enables the firms to attain excellence in two ways:
(a) By focusing on activities selected, their excellence in those activities increases.
(b) They excel by extending their capabilities through contracting out the remaining activities to them who excel in them. - Cost Reduction: In the age of globalization, cost reduction is of vital importance to survive in the market. Division of labour not only enhances quality but also reduces cost. For example, India is preferred as an outsourcing destination because of cost factors.
- Growth through alliance: When some activities are outsourced then these alliance partners invest for the outsourced activities. Business can be expanded by same amount of investible funds as now these funds are to be invested in limited number of activities.
- Fillip to Economic Development: Outsourcing stimulates entrepreneurship, employment and exports in the host countries. For example, in India there has been remarkable growth in entrepreneurship, employment and exports that today India is an undisputed leader in software development and IT enable services.
But outsourcing is not an unmixed blessing. It has its own limitations. Some of which are discussed below:
- Confidentiality: When a business opts for outsourcing, it has to share a lot of vital information and knowledge. This information may be leaked by the outsourcing partner. It may be against the outsourcing firm. It is also possible that the outsourcing partner starts a business of same line after getting such information.
- Ethical Concerns: Many a time, outsourcing makes use of child labour and violates labour laws to reduce costs. They also discriminate in wages on the basis of sex.
- Sweat Shopping: A firm which goes in for outsourcing actually transfers ‘doing’ skills rather than ‘thinking’ skills. Therefore, they do not create skilled manpower in developing countries but just take maximum benefit of low cost labour by transferring non intellectual tasks.
- Resentment in their Home Countries: Outsourcing is being disliked by people in developed countries because the jobs which they could get are being transferred to developing countries through outsourcing. The problem is still more severe if there is problem of unemployment in home country of outsourcing firm.
Question 4. Discuss the salient aspects of B2C commerce.
Answer: In this, both the parties involved are business firms and therefore, it has been named as B2B i.e., business to business. Historically, the term e-commerce originally meant for facilitation of B2B transactions using Electronic Data Interchange (EDI) technology to send and receive commercial documents like purchase orders and invoices. Salient aspects of B2B Commerce:
- Need: Creation of utility requires a business to contact with a number of other businesses which
- May be suppliers
- May act as channel of distribution.
- Different middlemen in different locations;
- Changing production as per specifications of the customer.
- Benefits:
- It strengthens and improves the distribution system of a firm. For example, each consignment of goods from a warehouse and the stock in hand can be monitored and replenishments and reinforcements can be set in motion as and when needed.
- A customer’s specifications can be routed through the dealers to the factory so that there may be customized production.
- B2B E-commerce expedites the movement of information and documents.
- It also expedites money transfers.
- Example: The manufacture of an automobile requires assembly of a large number of components which in turn are being manufactured elsewhere. To reduce dependence on a single vendor, the automobile factory cultivates more than one vendor for each of the components. A network of computers is used for placement of orders, controlling production and delivery of components and making payments.
Question 5. Discuss the limitations of electronic mode of doing business. Are these limitations severe enough to restrict its scope? Give reasons for your answer.
Answer: The limitations of electronic mode of doing business are given below:
- Low personal Touch: It lacks the warmth of interpersonal interactions. Therefore, such products which need personal touch like beauty products, garments, fashion accessories etc. can’t be traded through e-business.
- Mismatch between order giving/taking speed and order fulfillment speed: Sometimes websites take a long time to open which may frustrate the user. Even after giving or taking order, it takes enough time to give physical delivery of goods. It also plays on the patience of the customer.
- Knowledge of technology is must: For e-commerce both the parties need fairly high degree of familiarity with the world of computers. It divides the society into two parts i.e; one who are familiar with digital technology and other who are not.
- Increased risk due to parties being unknown to each other: When two parties are involved in e-business, they are unaware of personal identities of each other. They do not even know the locations of the parties involved. It makes e-business risky. There may also be problems of virus and hacking.
- People Resistance: People are resistant to change their ways and adopt new technology. Change is perceived as a source of stress and insecurity by many.
- Ethical Concerns: These days companies use an electronic eye to keep track of the websites being used by employees, computer files that they use, their e-mal accounts etc. It is not ethical.
But in spite of these limitations, e-business is the way. No, these limitations are not severe enough to restrict its scope.
- Improvement in Information Technology: With the improvement in information technology and emergence of internet the process of outsourcing and e-business is on an expansionary path. Anti virus and improved security measures are increasing to make e-business more secure and safer option.
- More and more Interactive Websites: Websites are becoming more and more interactive. It is removing the problem of ‘low personal touch’.
- Improvement in Communication Technology: Communication technology is continually evolving and increasing the speed and quality of communication through internet so that customer does not get frustrated in processing the order.
- Diffusion of E-Commerce in all nooks and corners of the country: An order to diffuse e-commerce in all nooks and corners, India has undertaken about 150 such projects. It is increasing the number of people acquainted with digital technology. We can conclude that e-business will continue to stay and reshape the businesses, governance and economies.
MORE QUESTIONS SOLVED
I. Multiple Choice Questions
Question 1. E-business and E-commerce are:
(a) Synonyms (b) Antonyms
(c) Former is wider than latter (d) Former is narrow than latter.
Question 2. When was Electronic Data Interchange (EDI) standardised?
(a) 1984 (b) 1995
(c) 2000 id) 1999
Question 3. In B2B, B2C, C2C etc B and C stand for:
(a) Business and Corporate (b) Biding and Customer
(c) Business and Customer (d) Business and Consumer
Question 4. When parties involved in the electronic transactions are from within a given business firm, it is called:
(a) B2B Commerce (b) Intra B Commerce
(c) C2C Commerce (d) B2C Commerce
Question 5. When a firm transacts with its employees, it is referred to as:
(a) B2B Commerce (b) B2E Commerce
(c) C2C Commerce (d) B2C Commerce
Question 6. Work from home using internet is covered under:
(a) Online Networking (b) Virtual Private Network
(c) Electronic Data Exchange (d) Paypal
Question 7. Which of the following is a benefit of e-business?
(a) Less Risky (b) Less Technological Requirements
(c) Convenience (d) All of the above
Question 8 Which of the following is not an application of e-business?
(a) E-procurement (b) e-bidding
(c) e-delivery (d) All of the above
Question 9. Which of the following can be used only for e-business?
(a) Cheques (b) Credit Card
(c) Debit Card (d) E-cash
Question 10. About 95% of online consumer transactions are executed through:
(a) Cheques (b) Credit Card
(c) Debit Card (d) E-cash
Question 11. When a customer claims that he has made payment but the seller does not get it, it is called:
(a) Default on Delivery (b) Default on Order Taking
(c) Bed Debts (d) Default on Payment
Question 12. Which of the following is used to handle data storage risk?
(a) VIRUS (b) Hacking
(c) Cryptography (d) All of the Above
Question 13. ——– is the largest captive BPO unit in India for providing certain kinds of services to the parent company in the United States as well as to its subsidiaries in other countries.
(a) Infosys (b) General electric (GE)
(c) Accenture (d) None of these
Question 14. BPO ———cost and———- excellence.
(a) Reduces, Reduces (b) Increases, Increases
(c) Reduces, Increases (d) Increases, Reduces
Question 15. InIndia————-and ——–are referred to as emerging modes of business.
(a) E-Business and E-Commerce (b) Outsourcing and E-business
(c) Outsourcing and E-Commerce (d) Online Trading and Networking.
Answers:
1. (c) 2. (a) 3. (d) 4. (b) 5. (b)
6. (b) 7. (c) 8. (d) 9. (d) 10. (b)
11. (d) 12. (c) 13. (b) 14. (c) 15. (c)
II. Short Answer Type Questions
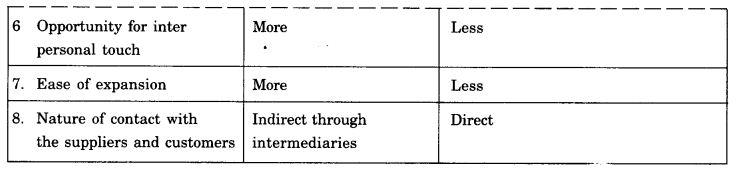
Question 1. Differentiate between traditional business and e-business.
Answer: Differences between traditional business and e-business is summarized below: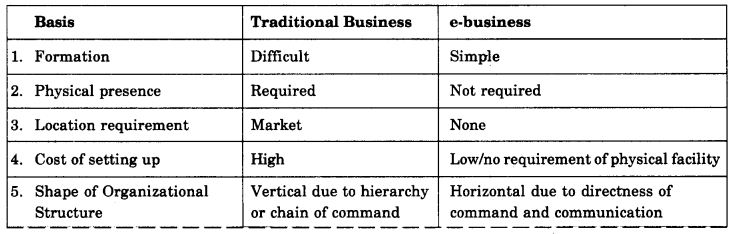
Question 2. Write a short note on the scope of e-business.
Answer: Scope of e-business is very wide. It is summarized below:
- B2B Commerce: Business to Business—Both the parties are business firms, e.g. Manufacturer of an automobile requires assembly of a large number of components which are being manufactured by different firms; Maruti Udyog, Bajaj Auto etc. use B2B commerce.
- B2C Commerce: Business to Customer—Transaction taking place between business and individual customers. It facilitates promotion of products on line. e.g. music or film. Companies sell products and services on line to customer e.g. Amul.com sell Amul products online.
- Intra – B. Commerce: Parties involved are from within a given business firm. It makes it possible for the marketing department to interact constantly with the production department to get information about customer requirement.
- C2C Commerce: Consumer to consumer—Business originates from the consumer and the ultimate destination is also consumer. Its area of application is the formation of consumer forum, e.g. selling used books over the internet.
Question 3. Write a short note on the history of e-commerce.
Answer: The origin of e-commerce dates back to electronic media like telephone, fax, compact disc, cable and personal computer etc. These electronic media had several limitations like speed, accuracy, secrecy, geographical distance, authenticity etc. Business transactions were carried out using electronic devices. Let us look at the history chronologically.
- In 1984, EDI or Electronic data interchange was standardized through ASC X12. It guaranteed that companies will be able to complete transactions with each other reliably.
- In 1992, ‘Compursive’ offered online retail products to its customers.
- In 1994, Netscape arrived which provided a simple browser to surf the internet and launched a safe online transaction technology called Secure Socket Layer (SSL).
- In 1995 two of the biggest names in e-commerce were launched namely, amazon.com and e-bay.com.
- In 1998, Digital Subscribed Line was launched.
- In 1999, retail spending over the internet reached $820 billion dollar as per business.com.
- In 2000, the USA government extended moratorium on internet taxes till 2005.
Question 4. Differentiate between e-commerce and e-business.
Answer: E-business and e-commerce are terms that are sometimes used interchangeably and sometimes they’re used to differentiate one vendor’s product from another. But the terms are different, and that difference matters to today’s companies.
Definition of E-Commerce
E-commerce is “any transaction completed over a computer-mediated network that involves the transfer of ownership or rights to use goods and services,” defines the U.S. Census Bureau. Transactions aren’t required to have a price and include both sales and items like free downloads. E-commerce includes transactions made on the internet, Intranet, Extranet, World Wide Web, by e-mail and even by fax.
Definition of E-Business
E-business is broader than e-commerce; including the transaction based e-commerce businesses and those who run traditionally but cater to online activities as well. An e-business can run any portion of its internal processes online, including inventory management, risk management, finance, human resources. For a business to be e-commerce and e-business, it must both sell products online and handle other company activities or additional sales offline.
- E-commerce covers outward-facing processes that touch customers, suppliers and external partners, including sales, marketing, order taking, delivery, customer service, purchasing of raw materials and supplies for production and procurement of indirect operating expense items, such as office supplies. E-business includes e-commerce but also covers internal processes such as production, inventory management, product development, risk management, finance, knowledge management and human resources.
- E-business strategy is more complex, more focused on internal processes, and aimed at cost savings and improvements in efficiency, productivity and cost savings than e-commerce.
- Scope of e-business is wider than e-commerce.
Question 5. What is digital divide? How is it relevant in context of e-business?
Answer: It is division of society on the basis of familiarity with digital technology and non-familiarity with digital technology. The digital divide causes a significant problem in many struggling parts of the world. “As of 2003, only seven per cent of the world’s 6.4 billion people have had access to the World Wide Web” [Ryder M, 2005]. The parts of the world that have a predominant amount of internet access is the Western World, the United States, Europe and Northern Asia, whereas access is more restricted in the poorer less developed parts of the world such as Africa, India and southern parts of Asia. These poorer nations are unable to afford the initial start up cost to be able to invest into technology to allow their nation to be able to have and maintain internet access. This puts these countries at a competitive and economic disadvantage. This is due to the fact that it impacts on society at many levels. By a country not having internet access, it means that schools are unable to teach IT skills and take advantage of the vast amount of information available on the web. With the lack of IT skills people from these countries are unable to compete at an international level.
Question 6. Explain various payment mechanisms under e-business.
Answer: Various payment mechanisms under e-business are described below:
- Cash on Delivery: Under this, the payment for goods ordered online may be made in cash at the time of physical delivery of the goods.
- Cheque: Another option is that the online vendor may arrange for the pickup of the cheque from the customer’s end. Upon realization, goods may be delivered.
- Net Banking Transfer: These days banks provide facility to the customers for electronic transfer of funds using internet. Therefore, a buyer can also make use of net banking money transfer to pay for the goods ordered.
- Credit or Debit Cards: These are also called plastic money. These cards are most popularly used in payment for online transactions. To accept credit card as an online payment type, the seller first needs a secure means of collecting credit card information from its customer. Payments through credit cards can be processed either manually, or through an online authorization system like SSL Certificate.
- Digital Cash: It is a kind of electronic currency which exists only in cyberspace. It has no real physical properties, but offers the ability to use real currency in an electronic format. For this the buyer has to deposit cash in bank account which issues equivalent digital cash to the person which can be used for online trading. It is more secure than credit or debit cards.
Question 7. Explain the measures taken to protect the security and safety of e-transactions.
Answer: Following measures are taken to protect security and safety of e-transactions:
- Cryptography: According to Pete Loshin, “It means use of such measures so as to keep the information out of the hand of anyone but its intended recipient. “Even if the message is intercepted the meaning shall not be apparent unless the interceptor is able to decode. This technique makes use of of codes and cyphers.
- Password: The parties to an e-commerce transaction must use the password.
Password is a code fed in computer by the user. It can be in alphabets or numeric or alpha-numeric characters. Unless a person feeds in the password, system shall neither respond nor give effect to the transactions. Therefore, one must keep a password. - Cookies: Cookies are very similar to creating ID in telephones that provide telecallers with such relevant information as the customer’s name, address and previous purchase payment record.
- Creating Keys: Key is a secret algorithm. Only the person who has the key can read the data.
Question 8. What resources are required for successful implementation of e-business?
Answer: Three m’s are required for setting up any business: men, money and machines:
For e-business some additional sources are required. It needs a website with allotted
cyberspace. More is the cyberspace, more is the cost of website and vice-versa. Space
requirement depends on scale of operations and how interactive a website is.
III.Long Answer Type Questions
Question 1. Show the anatomy of outsourcing.
Answer: Anatomy of outsourcing has been shown with the help of chart given below: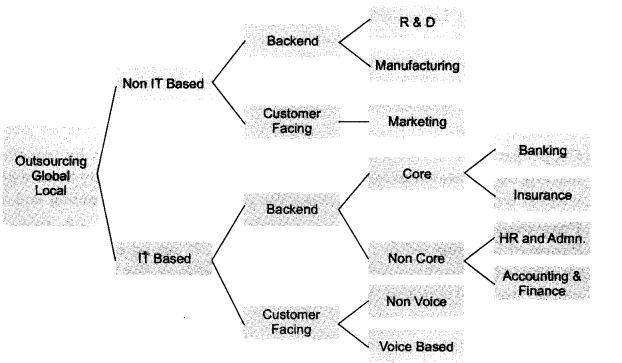
Question 2. What are the threats to e-transactions? Which measures have been devised for their protection?
Answer: There are many threats to e-transactions. Risk here is referring to probability of any mishappening that can result into financial, reputational or psychological losses to the parties involved in the transaction. It includes:
- Transaction risks: It can be of three types:
- Default on Order Taking or Giving: Seller denies that the customer ever placed the order or customer denies that he ever placed the order.
- Default on Delivery: It happens when either goods are delivered at a wrong address or wrong goods are delivered.
- Default on Payment: Seller does not get the payment for the goods delivered but customer claims that he has made the payment.
- Data Storage and Transmission Risks: Data stored in the systems and en route is exposed to a number of risks. Major two risks are related to virus and hacking. Virus is a program which replicates itself on the other computer systems. The effect of computer viruses can range from mere annoyance in terms of some on-screen display (level -1 virus), disruption of functioning (level-2 virus) damage to target data files (level-3 virus) to complete destruction of the system.(level-4 virus). Hacking refers to unauthorized logging into the account and misusing it for selfish purposes or for fun only. Antivirus can help to protect files from virus and cryptography is used for protection against hacking.
- Risks of threat to Intellectual Property and Privacy: Once an information is uploaded on internet, it loses privacy and IPRs. It becomes difficult to protect it from being copied and being accessible to one and all.
The following measures have been devised for their protection:
- Secure Socket Layer (SSL): It was designed by Netscape for use in electronic commerce for transactions involving confidential information like credit card numbers. SSL uses a system of public and private key authentication combined with schemes to verify electronic signatures. Public key is the password that the sender uses to encrypt the data and the private key is used by the receiver of a message to descrypt the data.
- Cryptography: It refers to the art of protecting information by transforming it (encrypting it) into an unreadable format called ‘cyphertext’. Only those who possess a secret key can decrypt the message into plain text. It is like coding and decoding.
- Password: The parties to an e-commerce transaction must use the password. Password is a code fed in computer by the user. It can be in alphabets or numeric or alpha-numeric characters. Unless a person feeds in the password, system shall neither respond nor give effect to the transactions. Therefore, one must keep a password.
- Cookies: Cookies are very similar to creating ID in telephones that provide telecallers with such relevant information as the customer’s name, address and previous purchase payment record.
- Anti-virus: There are anti-viruses which remove any type of virus from the system.
IV. Higher Order Thinking Skills (HOTS)
Question 1. “E-commerce is the need of the hour.” Comment.
Answer: In this century, lifestyle has undergone a drastic change. People have everything except time. Using e-commerce they can buy and sell almost everything at your doorstep with the magic of e-commerce in the 21st century which will be known for information revolution. E-commerce has changed your lifestyles entirely because you don’t have to spend time and money in travelling to the market. You can do your e-payments with the help of e-commerce.
There is no time barrier in selling the products. One can log on to the internet even at midnight and can sell the products at a single click of mouse. E-commerce reduces delivery time and labor cost. Thus it has been possible to save the time of both-the vendor and the consumer.
Its need is clear from its benefits given below:
- Exploitation of New Business: Broadly speaking, electronic commerce emphasizes the generation and exploitation of new business opportunities and to use popular phrases: “generate business value” or “do more with less”
- Enabling the Customers: Electronic Commerce is enabling the customer to have an increasing say in what products are made, how products are made and how services are delivered (movement from a slow order fulfillment process with little understanding of what is taking place inside the firm, to a faster and explore open process with customers having greater control.
- Improvement of Business Transaction: Electronic Commerce endeavors to improve the execution of business transaction over various networks.
- Effective Performance: It leads to more effective performance i.e., better quality, greater customer satisfaction and better corporate decision making.
- Greater Economic Efficiency: We may achieve greater economic efficiency (lower cost) and more rapid exchange (high speed, accelerated, or real-time interaction) with the help of electronic commerce.
- Execution of Information: It enables the execution of information laden transactions between two or more parties using interconnected networks. These networks can be a combination of ‘plain old telephone system’ (POTS), Cable TV, leased lines and wireless. Information based transactions are creating new ways of doing business and even new types of business.
- Facilitating of Network Form: Electronic Commerce is also impacting business to business interactions. It facilitates the network form of organization where small flexible firms rely on other partner, companies for component supplies and product distribution to meet changing customer demand more effectively. Hence, an end to end relationship management solution is a desirable goal that is needed to manage the chain of networks linking customers, workers, suppliers, distributors and even competitors. The management of “online transactions” in the supply chain assumes a central roll.
Question 2. “E-commerce is giving way to paperless society and government is supporting it.” Substantiate.
Answer: It is right to say that E-commerce is giving way to paperless society. Government is also formulating laws to help in this creation. It is clear from the laws formulated under IT Act, 2000:
- Legal recognition of electronic records: Where any law provides that information or any other matter shall be in writing or in the typewritten or printed form, then, notwithstanding anything contained in such law, such requirement shall be deemed to have been satisfied if such information or matter is rendered or made available in an electronic form; and accessible so as to be usable for a subsequent reference. For example, a company can send notice for AGM using e-mail.
- Retention of electronic records: Where any law provides that documents, records or information shall be retained for any specific period, then, that requirement shall be deemed to have been satisfied if such documents, records or information Eire retained in the electronic form. For example, if results are preserved in electronic form it will work.
- Legal recognition of digital signatures: Where any law provides that information or any other matter shall be authenticated by affixing the signature or any document shall be signed or bear the signature of any person, hence notwithstanding anything contained in such law, such requirement shall be deemed to have been satisfied, if such information or matter is authenticated by means of digital signature affixed in such a manner as may be .prescribed by the Central Government.
- Use of electronic records and digital signatures in Government and its agencies: Where any law provides for the filling of any form, application or any other document with any office, authority, body or agency owned or controlled by the appropriate government in a particular manner; the issue or grant of any license, permit, sanction or approval by whatever name called in a particular manner; the receipt or payment of money in a particular manner, then, notwithstanding anything contained in any other law for the time being in force, such requirement shall be deemed to have been satisfied if such filing, issue, grant, receipt or payment, as the case may be, is effected by means of such electronic form as may be prescribed by the appropriate government. All these provisions of IT Act, 2000 are helping us to move towards a paperless society.
Question 3. Discuss the utility of E-Commerce in:
(a) Health,
(b) Education,
(c) Governance,
Answer: (a) Changes in Health: E-health is following the same path, with electronic patient records slowly being introduced and health insurance schemes starting to refund e-health services. This will be a user driven development as it is more likely that the users will be able to adapt to e-health much faster than the healthcare system can deliver it.
This will clear the way for a whole new e-health industry, worth billions of dollars. One has to look at some of the e-health systems linked to the high end private hospitals in the USA to see what is in store. They use their e-health facilities as a major marketing tool to attract customers, not just to the actual hospital, but to all the other facilities around it. The add on revenues are significant.
(b) Progress in e-education: It is moving at an enormous pace and already some schools are limiting the number of printed textbooks – some are going totally e-book. With over a million children now with laptops it is only a matter of time before the education system to switch over. The savings in books and other printed material alone will pay for this digital revolution. South Korean schools will be entirely e-book-based by 2015.
(c) Governance: Many e-government services on offer around the world already provide citizens with relatively sophisticated services and the establishment of a fiber based broadband network may see governments improve and broaden the range of web services even further. In addition, mobile services are being incorporated in service offerings and computing is becoming integrated. The Internet of Things (IoT) and M2M wifi also impact upon this sector. Those who are still talking about broadband as an end in itself; do not understand the situation. Broadband is simply the tool that will further enable and advance the digital economy.
V. Value Based Questions
Question 1. Which values are of utmost importance while we get involved in e-business?
Answer: Following values are of utmost importance when we get involved in e-business:
- Confidentiality: We must keep information of our clients confidential.
- Business ethics: Electronic eye should not be kept for personal usage. Its use must be minimized only for critical situations and in critical areas.
- No Undesirable Information: Our website must not advertise or promote any such thing which is not desirable from society point of view.
- Take all safety precautions: We must take safety precautions to ensure safety of data and to protect against risks of data storage.
Question 2. Hackers lack certain values. Which are these?
Answer: It will not be wrong to say that hackers lack certain values:
- They do not value the importance of other persons privacy.
- They are keen to use others efforts for their selfish means and even for fun.
- They wish to get many things without putting an effort for it using short cuts and illegal means.
But remember in exceptional cases, hacking is also used to find criminals and to solve criminal cases.










